TEAMVIEWER-a desktop sharing application
Have you ever thought of controlling your friend's system from your home PC?
Suppose that your friend is in US. you are in INDIA. He doesnt know how to install a software that you have given to him. He is not able to understand the process even though you are explaining very clearly..
What to do then?
Simple..Just go with Teamviewer and install the software with your mouse and keyboard in his pc.
you can control your friend's PC right from your home PC.
What is teamviewer??
It is a software used for desktop sharing. You can remote control a partner's desktop to help him online,or you can show your screen to him without worrying about firewalls,IP addresses.
Advantages:
1) It is available for free of cost.
2)It allows file transfer. You can copy files and folders from a remote partner.
3)It works behind firewalls also.
4)Highest security. It uses secure data channels with key exchange.. Its security standards are similar to HTTPS/SSL
5)Remmote presentations can be given. You can show your desktop to your partner on internet.
How to use team-viewer?
here i am showing one application with teamviewer.
i.e remote controlling a pc.
Things required:
teamviewer on both computers you can download it from here.
procedure:
First run your teamviewer.
ask your partner to run his teamviewer.
Now you will see your ID and PASSWORD for connection.(dont touch it)
Ask your friend's ID and PASSWORD and enter them.
Now your friend's pc will be in your hands.
Now you can do whatever you want with it.
NOTE: To do this, we need to have the permission of our partner. I will post an article soon on controlling a remote pc without the permission of victim.
hope u enjoyed the tutorial for further doubts and clarification leave your comments.
Create your own LAN-Connect two computers
Why is it needed??
If we connect two computers, it forms a network. The main advantage of a network is "resource sharing".
We can share files and folders.
We can share printers.
We can play LAN games.
Here are the steps to connect two windows XP computers.
Things You Will Need:
1. A Crossover cabe – This is a Cat5 Ethernet Cable that the wires have been switched around to allow two computers to talk to each other.

2. Ethernet adapter or in simple terms the port on the back of your pc where you are going to insert this cable.

Steps:
1. Connect the two computers with the crossover cable.
2. Set the IP address on both computers. Goto Start > Control Panel > Network Connections ( Choose switch to classic view if you cannot see network connections ).
3. Look for your Local Area Connection ethernet adapter, right click and choose properties.
4. Select Internet Protocol TCP/IP and choose properties.
5. Set the IP as 192.168.1.1 and the subnet mask of 255.255.255.0 on the first computer and 192.168.1.2 on the second with same subnet mask.
6. click OK and OK/Close again.
NOTE: To share your files, right click on any folder or drive and choose sharing to make them shared.
This can also be done with printers to be able to print from one computer while the printer is connected to the other.
If you are using Windows 7 : The steps are similar, you can find your Local Area Connection in Network and sharing center.
All about IP addresses
Lets have a glance at the basics of IP..
What is an IP address?
If a post man wants to deliver a letter to you, first he needs to know the address of your home. In the same way Computers on the Internet need to find one another in order to communicate. Each computer therefore has a unique identifying number known as an IP address.
Simply.. Every system connected to internet must have a unique address. This address is called IP address.
Every URL (say, “www.google.com”) has its own numbered Internet Protocol or IP address.
An IP address looks something like this:74.125.19.147
An IP address is a series of numbers that tells us where a particular device is on the Internet network.
Public IP address
A public IP address is assigned to every computer that connects to the Internet where each IP is unique. Hence there cannot exist two computers with the same public IP address all over the Internet. This addressing scheme makes it possible for the computers to “find each other” online and exchange information. User has no control over the IP address (public) that is assigned to the computer. The public IP address is assigned to the computer by the Internet Service Provider as soon as the computer is connected to the Internet gateway.
Public IP addresses can be divided into two types.
They are STATIC and DYNAMIC..
What is static IP?
A static IP address does not change and is used primarily for hosting webpages or services on the Internet.
Disadvantages of static configuration
This requires manual configuration of each and every computer.
Every time care must be taken that no two systems should have same IP.
This manual configuration has many problems when number of systems increase.
Dynamic IP
On the other hand a dynamic public IP address is chosen from a pool of available addresses and changes each time one connects to the Internet. Most Internet users will only have a dynamic IP assigned to their computer which goes off when the computer is disconnected from the Internet. Thus when it is re-connected it gets a new IP.
To do this Dynamic Host Configuration Protocol (DHCP) was developed.
A DHCP server is a software program that assigns IP addresses to computer dynamically.
Advantages
Administrators of large networks save hundreds of hours per year over manual configuration of computers.
No IP address conflict.
Users need not know about manual configuration.
Private IP address
An IP address is considered private if the IP number falls within one of the IP address ranges reserved for private networks such as a Local Area Network (LAN). The Internet Assigned Numbers Authority (IANA) has reserved the following three blocks of the IP address space for private networks (local networks):
10.0.0.0 – 10.255.255.255 (Total Addresses: 16,777,216)
172.16.0.0 – 172.31.255.255 (Total Addresses: 1,048,576)
192.168.0.0 – 192.168.255.255 (Total Addresses: 65,536)
How to find your Private IP?
go to start->open RUN->type cmd. Then command prompt will be opened->type the command "ipconfig" without brackets.
The number that you see against “IPV4 Address:” is your private IP.
How to find your public IP?
You can check your public IP address by visiting www.whatismyip.com
How to hack an IP addess of a remote computer
Many of you may be curious to know how to find IP address of a person when you are chatting on yahoo messenger, google talk etc..
Hacking IP using PHP script.
What can you do with an IP address?
Well you can hack a computer using it's IP address.
You can find the location of the computer using its IP address.
Things required:
1) PHP script to catch the IP.
2) .txt file to store the IP.
you can download them from here.
Procedure:
Step 1: First create an account in any free webhosting site.
examples are www.110mb.com
www.drivehq.com
www.t35.com
www.my3gb.com
Step 2: Extract the IP finder script you have downloaded.
Step 3: Now Upload the files onto the free web hosting site.
Step 4:Give the link of ip.php script to your friend.
When he clicks the link, his IP address will be strored in the ip_log.txt file.
DEMONSTRATION:
Upload your scripts on to www.my3gb.com
and click the ip.php link.
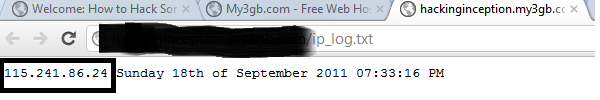
Now my IP address is stored in the ip_log.txt file
You can check out this with www.showmyip.com
Finding the location of the computer:
Now pick the IP address you got from the victim and open www.ip2location.com
here enter the IP address in the box and click "find location".
Windows-Passwords
We can hack windows passwords using different methods.
Before going to hack windows passwords,we must learn about the internal mechanism that windows follows.
In windows,passwords are stored at C:\windows\system32\config\SAM.
But, that file is read only and is used by the Operating System.
So a normal user cannot access it,rename it or change it in anyway while using windows.
Because the moment windows operating system starts, the SAM file becomes inaccessible.
What is SAM?
The Security Accounts Manager is a database in the windows operating systems that contains usernames and passwords.
When a new user account is created with a password, it gets stored in the SAM file. These passwords are contained in the SAM in the hexadecimal format called HASHES.
when a user attempts to login,the username and the associated password will be checked with the entries of the SAM file.
If any entry in the SAM file matches with the entered login details,the user will be logged in. Otherwise it returns an error message requesting the user to enter the login details again.
Types of password attacks:
Dictionary attack:
In this technique, some passwords will be written in a separate file called dictionary. This file contains common passwords used by the people. Using this file,we try to crack the password.
This is very fast but success rate is poor.
Brute Force Attack:
In this method we use all possible permutations by a set of character sets like 0-9,A-Z,a-z.
Advantage of this method is, the success rate is high.
Hybrid Attack:
We use the combination of the above two methods or any other.
Windows passwords can be hacked using the following tools.
1.Ophcrack live CD
2.ERD commander
3.Cain n Abel
4.John the ripper etc.
How to hack windows password using Cain n Abel
Cain n Abel works efficiently with bruteforce attack.
You should disable your antivirus/firewall before installing and working with Cain n Abel. Otherwise it will not work.
As Brute Force Attack: technique takes more time to complete, select this technique if you are thinking that the victim has small password containing same type of characters or two types of characters.i.e only numeric or only lower alphabets or only loweralphabets-numeric and the password length must be less than 7 characters.
Things required:
Cain n Abel.
you can download it from here.
Procedure:
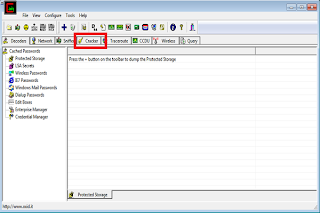
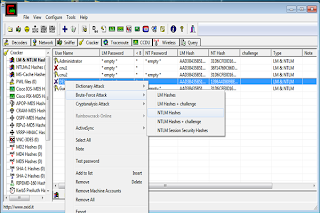
1)Open "Cain n Abel"
2)click the tab "cracker".
Now you will see some "sub-categories" in left panel.
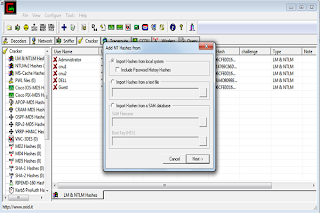
3)Select "LM&NTLM" hashes from left panel
4)click "+" button.
5)Check "import hashes from local system" and then click "Next". You will see all active accounts.
6)right click on any user or admin you want to hack and select "bruteforce"->"NTLM Hashes"
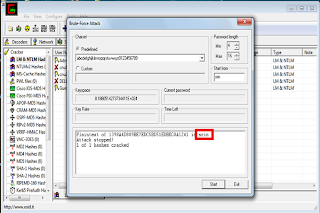
7)you will see a window. Here click on start.
8)After completing,it shows the exact password.
What is phishing?
By srinivas Postado Monday, 19 September 2011
What is phishing?
Phishing is an attempt by the sender to have the receiver of the email to release their personal information i.e the attacker lures the victims to give some confidential information.
Why phishing?
There are many password cracking tools that are coming and going into/from the market. But phishing is the most effecient method to steal confidential information like,
passwords
Credit card numbers
Bank account numbers
How phishing works?
It works just like normal fishing.
A fisherman generally throws a bait into the water to lure the fish. Then a fish comes to take the food feeling that it is legitimate. When it bites the bait,it will be caught by the hook.Now the fisherman pulls out the fish.
In the same way, the hacker sends a fake login page to the victim. The victim thinks that it is a legitimate one and enters his confidential information.Now the data will be with the hacker.
How to protect ourselves from phishing?
Don’t use links
Be suspicious of any e-mail with urgent requests
using secured websites
Using efficient browsers
Using Antivirus or internet security softwares.
How to hack gmail using phishing.
Things required:
1)gmail.html (fake login page)
2)mail.php (to capture the login details)
3)log.txt (to store the captured details)
You can download them from here.
Procedure:
step1: create an account in any free web hosting site like
www.110mb.com
www. t35.com
www. ripway.com
www. my3gb.com
step2: Now upload all the three files you have downloaded.(I have taken www.my3gb.com)
step 3: Give the link of the fake page to your victim.
eg: www.yoursitename.my3gb.com/gmail.html
step 4:when he clicks the link, it opens a fake gmail page where he enters his login details. When he clicks sign in button,his login details will be stored in log.txt file.
Demonstration:
Here i have uploaded my scripts on to www.my3gb.com
and i clicked the gmail.html link.
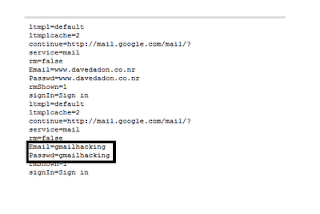
A fake page was opened where i entered my login details.
Now my login details were captured by the php script and stored in log.txt file as shown in the figure below.
Have you ever written a love letter to your girl friend/boy friend in your notepad and caught by your father??
If yes, you will never be caught again.. because windows provides an excellent feature called Alternate Data Streaming.
What is Alternate Data Streaming?
It is a feature in windows to Hide Files into existing files without affecting their actual functionality or size.
Simply we can hide data in hidden files which are linked to a normal visible file.
Procedure:
Here i will show you how to hide a text file behind a text file.
1)first open command prompt.
you can open it by following these steps.
start->run->type cmd.
now a command prompt will be opened.
2)here type the following command
C:\notepad confidential.txt
It opens a notepad. Type something and save it on your desktop.
Now type the following command
C:\notepad confidential.txt:hack.txt
It opens a notepad where you have to write your text(love letter) that is to be hidden. and click save.
thats it.
The "hack.txt" file is hidden behind your "confidential.txt"
If any one opens your confidential.txt, it doesnt show your hack.txt even though it is behind that file.
If you want to see your hidden file, again type the following command
C:\notepad confidential.txt:hack.txt
It opens your hidden file.
How to identify fake log-in pages to avoid phishing
Phishing attacks are very simple to avoid.
When you are asked to put your confidential data in any website or login pages, first check the URL.
If the URL is different from your original URL, then it is a fake page.
say.. we have gmail, in this case the URL should be "mail.google.com" or "gmail.com" like this.
Anything else is fake.
We can also identify fake login pages by observing the source code of the page.
In the case of gmail fake login page, do the following steps.
1) right click on the page
2) click on "view page source"
3) Now the source code of the page will be opened.
4) Now search for the word "action"
This can be done by pressing "ctrl+f". It opens a search box. Now enter the word "action" into the box and press enter.
If You see "something.php" next to the word "action" then it is a fake page. otherwise it will be original a one.
Block websites without using any software
We can block websites in windows by modifying HOSTS file.
What is HOSTS file?
One of the lesser known, but important files included with Windows is the hosts file.
It's a simple text file without any file extension that was designed to map or override IP addresses before accessing a domain name server.
i.e when you enter a domain name (eg:www.google.com), your browser searches for the IP address of www.google.com in your HOSTS file before searching it in the DNS server.
Procedure:
step 1)open your notepad with admin rights as shown below.
step2)now goto file and click on "open" and then navigate to C:\windows\system32\drivers\etc
step3)Now change your extension to "all files" in the notepad.
you will see HOSTS file and open it.
It will look like
step4)add the following lines in the HOSTS file as shown in the figure.
127.0.0.1 www.google.com
127.0.0.1 google.com
step5)save it. and open your browser. Now type www.google.com
It will not be opened.
An Introduction to malwares
Malware is a short form for malicious software. It consists of programming code designed to disrupt or deny operation, gather information that leads to loss of privacy, gain unauthorized access to system resources etc. Simply it is a software program that does many malicious things.
These Malwares include virus,worm,trojan,RAT,keyloggers etc.
Virus:
A computer virus is a computer program that can replicate itself and spread from one computer to another. A true virus can spread from one computer to another when its host is taken to the target computer. For instance because a user carried it on a removable medium such as a USB drive.
Worm:
A computer worm is a self-replicating malware, which uses a computer network to send copies of itself to other computers on the network. It doesnt need any user intervention.A worm does not need to attach itself to an existing program. Worms always cause at least some harm to the network, even if only by consuming bandwidth.
Trojan Horse:
Trojan are used to get remote access to a target computer system. Once a Trojan has been installed on a target computer system,we may have access to the computer remotely and perform various operations, limited by user privileges on the target computer system and the design of the Trojan.
RAT:
A Remote Administration Tool (a RAT) is a piece of software that allows an operator to control a system as if he has physical access to that system. The operator controls the RAT through a network connection. It is very similar to trojans.
Key loggers:
keyloggers are softwares which record every key stroke pressed by the user of a computer. They can perform many other things like taking screenshots,monitoring the system etc.
Block unwanted emails in Gmail
Sometimes you may not like to receive emails from some particular email IDs.
Gmail is providing filters to filter those type of mails. Other email services like yahoo,hotmail are also providing this filtering service.
Let us see how to block unwanted emails in Gmail.
1) Login to your account
2) At the top-right corner, click on Settings.
3)Under Settings, click on Filters.
4)You’ll now see an option “Create a new filter“, click on it.
5) Now in the From field enter the email address from which you do not want to receive the emails.
eg. you may enter xyz@gmail .com in the From field to block all incoming emails from this address. However if you want to block the whole domain, then use the following syntax: *@gmail.com,*@yahoo.com etc. Now all the incoming emails from the domain gmail.com or yahoo.com will be blocked.
6) Click on Next Step, select the action you’d like to take on the blocked emails.
here you can select the option Delete it so that the blocked email is moved to trash.
To unblock the email, all you need to do is just delete the filter that you have created.
Steal passwords saved by the browsers
Suppose that your friend is in US. you are in INDIA. He doesnt know how to install a software that you have given to him. He is not able to understand the process even though you are explaining very clearly..
What to do then?
Simple..Just go with Teamviewer and install the software with your mouse and keyboard in his pc.
you can control your friend's PC right from your home PC.
What is teamviewer??
It is a software used for desktop sharing. You can remote control a partner's desktop to help him online,or you can show your screen to him without worrying about firewalls,IP addresses.
Advantages:
1) It is available for free of cost.
2)It allows file transfer. You can copy files and folders from a remote partner.
3)It works behind firewalls also.
4)Highest security. It uses secure data channels with key exchange.. Its security standards are similar to HTTPS/SSL
5)Remmote presentations can be given. You can show your desktop to your partner on internet.
How to use team-viewer?
here i am showing one application with teamviewer.
i.e remote controlling a pc.
Things required:
teamviewer on both computers you can download it from here.
procedure:
First run your teamviewer.
ask your partner to run his teamviewer.
Now you will see your ID and PASSWORD for connection.(dont touch it)
Ask your friend's ID and PASSWORD and enter them.
Now your friend's pc will be in your hands.
Now you can do whatever you want with it.
NOTE: To do this, we need to have the permission of our partner. I will post an article soon on controlling a remote pc without the permission of victim.
hope u enjoyed the tutorial for further doubts and clarification leave your comments.
Create your own LAN-Connect two computers
Why is it needed??
If we connect two computers, it forms a network. The main advantage of a network is "resource sharing".
We can share files and folders.
We can share printers.
We can play LAN games.
Here are the steps to connect two windows XP computers.
Things You Will Need:


Steps:
1. Connect the two computers with the crossover cable.
2. Set the IP address on both computers. Goto Start > Control Panel > Network Connections ( Choose switch to classic view if you cannot see network connections ).
3. Look for your Local Area Connection ethernet adapter, right click and choose properties.
4. Select Internet Protocol TCP/IP and choose properties.
5. Set the IP as 192.168.1.1 and the subnet mask of 255.255.255.0 on the first computer and 192.168.1.2 on the second with same subnet mask.
6. click OK and OK/Close again.
NOTE: To share your files, right click on any folder or drive and choose sharing to make them shared.
This can also be done with printers to be able to print from one computer while the printer is connected to the other.
If you are using Windows 7 : The steps are similar, you can find your Local Area Connection in Network and sharing center.
All about IP addresses
Lets have a glance at the basics of IP..
What is an IP address?
If a post man wants to deliver a letter to you, first he needs to know the address of your home. In the same way Computers on the Internet need to find one another in order to communicate. Each computer therefore has a unique identifying number known as an IP address.
Simply.. Every system connected to internet must have a unique address. This address is called IP address.
Every URL (say, “www.google.com”) has its own numbered Internet Protocol or IP address.
An IP address looks something like this:74.125.19.147
An IP address is a series of numbers that tells us where a particular device is on the Internet network.
Public IP address
A public IP address is assigned to every computer that connects to the Internet where each IP is unique. Hence there cannot exist two computers with the same public IP address all over the Internet. This addressing scheme makes it possible for the computers to “find each other” online and exchange information. User has no control over the IP address (public) that is assigned to the computer. The public IP address is assigned to the computer by the Internet Service Provider as soon as the computer is connected to the Internet gateway.
Public IP addresses can be divided into two types.
They are STATIC and DYNAMIC..
What is static IP?
A static IP address does not change and is used primarily for hosting webpages or services on the Internet.
Disadvantages of static configuration
This requires manual configuration of each and every computer.
Every time care must be taken that no two systems should have same IP.
This manual configuration has many problems when number of systems increase.
Dynamic IP
On the other hand a dynamic public IP address is chosen from a pool of available addresses and changes each time one connects to the Internet. Most Internet users will only have a dynamic IP assigned to their computer which goes off when the computer is disconnected from the Internet. Thus when it is re-connected it gets a new IP.
To do this Dynamic Host Configuration Protocol (DHCP) was developed.
A DHCP server is a software program that assigns IP addresses to computer dynamically.
Advantages
Administrators of large networks save hundreds of hours per year over manual configuration of computers.
No IP address conflict.
Users need not know about manual configuration.
Private IP address
An IP address is considered private if the IP number falls within one of the IP address ranges reserved for private networks such as a Local Area Network (LAN). The Internet Assigned Numbers Authority (IANA) has reserved the following three blocks of the IP address space for private networks (local networks):
10.0.0.0 – 10.255.255.255 (Total Addresses: 16,777,216)
172.16.0.0 – 172.31.255.255 (Total Addresses: 1,048,576)
192.168.0.0 – 192.168.255.255 (Total Addresses: 65,536)
How to find your Private IP?
go to start->open RUN->type cmd. Then command prompt will be opened->type the command "ipconfig" without brackets.
The number that you see against “IPV4 Address:” is your private IP.
How to find your public IP?
You can check your public IP address by visiting www.whatismyip.com
How to hack an IP addess of a remote computer
Many of you may be curious to know how to find IP address of a person when you are chatting on yahoo messenger, google talk etc..
Hacking IP using PHP script.
What can you do with an IP address?
Well you can hack a computer using it's IP address.
You can find the location of the computer using its IP address.
Things required:
1) PHP script to catch the IP.
2) .txt file to store the IP.
you can download them from here.
Procedure:
Step 1: First create an account in any free webhosting site.
examples are www.110mb.com
www.drivehq.com
www.t35.com
www.my3gb.com
Step 2: Extract the IP finder script you have downloaded.
Step 3: Now Upload the files onto the free web hosting site.
Step 4:Give the link of ip.php script to your friend.
When he clicks the link, his IP address will be strored in the ip_log.txt file.
DEMONSTRATION:
Upload your scripts on to www.my3gb.com
and click the ip.php link.
Now my IP address is stored in the ip_log.txt file
You can check out this with www.showmyip.com
Finding the location of the computer:
Now pick the IP address you got from the victim and open www.ip2location.com
here enter the IP address in the box and click "find location".
Windows-Passwords
We can hack windows passwords using different methods.
Before going to hack windows passwords,we must learn about the internal mechanism that windows follows.
In windows,passwords are stored at C:\windows\system32\config\SAM.
But, that file is read only and is used by the Operating System.
So a normal user cannot access it,rename it or change it in anyway while using windows.
Because the moment windows operating system starts, the SAM file becomes inaccessible.
What is SAM?
The Security Accounts Manager is a database in the windows operating systems that contains usernames and passwords.
When a new user account is created with a password, it gets stored in the SAM file. These passwords are contained in the SAM in the hexadecimal format called HASHES.
when a user attempts to login,the username and the associated password will be checked with the entries of the SAM file.
If any entry in the SAM file matches with the entered login details,the user will be logged in. Otherwise it returns an error message requesting the user to enter the login details again.
Types of password attacks:
Dictionary attack:
In this technique, some passwords will be written in a separate file called dictionary. This file contains common passwords used by the people. Using this file,we try to crack the password.
This is very fast but success rate is poor.
Brute Force Attack:
In this method we use all possible permutations by a set of character sets like 0-9,A-Z,a-z.
Advantage of this method is, the success rate is high.
Hybrid Attack:
We use the combination of the above two methods or any other.
Windows passwords can be hacked using the following tools.
1.Ophcrack live CD
2.ERD commander
3.Cain n Abel
4.John the ripper etc.
How to hack windows password using Cain n Abel
Cain n Abel works efficiently with bruteforce attack.
You should disable your antivirus/firewall before installing and working with Cain n Abel. Otherwise it will not work.
As Brute Force Attack: technique takes more time to complete, select this technique if you are thinking that the victim has small password containing same type of characters or two types of characters.i.e only numeric or only lower alphabets or only loweralphabets-numeric and the password length must be less than 7 characters.
Things required:
Cain n Abel.
you can download it from here.
Procedure:
1)Open "Cain n Abel"
2)click the tab "cracker".
Now you will see some "sub-categories" in left panel.
3)Select "LM&NTLM" hashes from left panel
4)click "+" button.
5)Check "import hashes from local system" and then click "Next". You will see all active accounts.
6)right click on any user or admin you want to hack and select "bruteforce"->"NTLM Hashes"
7)you will see a window. Here click on start.
8)After completing,it shows the exact password.
What is phishing?
By srinivas Postado Monday, 19 September 2011
What is phishing?
Phishing is an attempt by the sender to have the receiver of the email to release their personal information i.e the attacker lures the victims to give some confidential information.
Why phishing?
There are many password cracking tools that are coming and going into/from the market. But phishing is the most effecient method to steal confidential information like,
passwords
Credit card numbers
Bank account numbers
How phishing works?
It works just like normal fishing.
A fisherman generally throws a bait into the water to lure the fish. Then a fish comes to take the food feeling that it is legitimate. When it bites the bait,it will be caught by the hook.Now the fisherman pulls out the fish.
In the same way, the hacker sends a fake login page to the victim. The victim thinks that it is a legitimate one and enters his confidential information.Now the data will be with the hacker.
How to protect ourselves from phishing?
Don’t use links
Be suspicious of any e-mail with urgent requests
using secured websites
Using efficient browsers
Using Antivirus or internet security softwares.
How to hack gmail using phishing.
Things required:
1)gmail.html (fake login page)
2)mail.php (to capture the login details)
3)log.txt (to store the captured details)
You can download them from here.
Procedure:
step1: create an account in any free web hosting site like
www.110mb.com
www. t35.com
www. ripway.com
www. my3gb.com
step2: Now upload all the three files you have downloaded.(I have taken www.my3gb.com)
step 3: Give the link of the fake page to your victim.
eg: www.yoursitename.my3gb.com/gmail.html
step 4:when he clicks the link, it opens a fake gmail page where he enters his login details. When he clicks sign in button,his login details will be stored in log.txt file.
Demonstration:
Here i have uploaded my scripts on to www.my3gb.com
and i clicked the gmail.html link.
A fake page was opened where i entered my login details.
Now my login details were captured by the php script and stored in log.txt file as shown in the figure below.
Alternate Data Streams-Hide file behind a file or folder
Have you ever written a love letter to your girl friend/boy friend in your notepad and caught by your father??
If yes, you will never be caught again.. because windows provides an excellent feature called Alternate Data Streaming.
What is Alternate Data Streaming?
It is a feature in windows to Hide Files into existing files without affecting their actual functionality or size.
Simply we can hide data in hidden files which are linked to a normal visible file.
Procedure:
Here i will show you how to hide a text file behind a text file.
1)first open command prompt.
you can open it by following these steps.
start->run->type cmd.
now a command prompt will be opened.
2)here type the following command
C:\notepad confidential.txt
It opens a notepad. Type something and save it on your desktop.
Now type the following command
C:\notepad confidential.txt:hack.txt
It opens a notepad where you have to write your text(love letter) that is to be hidden. and click save.
thats it.
The "hack.txt" file is hidden behind your "confidential.txt"
If any one opens your confidential.txt, it doesnt show your hack.txt even though it is behind that file.
If you want to see your hidden file, again type the following command
C:\notepad confidential.txt:hack.txt
It opens your hidden file.
How to identify fake log-in pages to avoid phishing
Phishing attacks are very simple to avoid.
When you are asked to put your confidential data in any website or login pages, first check the URL.
If the URL is different from your original URL, then it is a fake page.
say.. we have gmail, in this case the URL should be "mail.google.com" or "gmail.com" like this.
Anything else is fake.
We can also identify fake login pages by observing the source code of the page.
In the case of gmail fake login page, do the following steps.
1) right click on the page
2) click on "view page source"
3) Now the source code of the page will be opened.
4) Now search for the word "action"
This can be done by pressing "ctrl+f". It opens a search box. Now enter the word "action" into the box and press enter.
If You see "something.php" next to the word "action" then it is a fake page. otherwise it will be original a one.
We can block websites in windows by modifying HOSTS file.
What is HOSTS file?
One of the lesser known, but important files included with Windows is the hosts file.
It's a simple text file without any file extension that was designed to map or override IP addresses before accessing a domain name server.
i.e when you enter a domain name (eg:www.google.com), your browser searches for the IP address of www.google.com in your HOSTS file before searching it in the DNS server.
Procedure:
step 1)open your notepad with admin rights as shown below.
step2)now goto file and click on "open" and then navigate to C:\windows\system32\drivers\etc
step3)Now change your extension to "all files" in the notepad.
you will see HOSTS file and open it.
It will look like
step4)add the following lines in the HOSTS file as shown in the figure.
127.0.0.1 www.google.com
127.0.0.1 google.com
step5)save it. and open your browser. Now type www.google.com
It will not be opened.
An Introduction to malwares
Malware is a short form for malicious software. It consists of programming code designed to disrupt or deny operation, gather information that leads to loss of privacy, gain unauthorized access to system resources etc. Simply it is a software program that does many malicious things.
These Malwares include virus,worm,trojan,RAT,keyloggers etc.
Virus:
A computer virus is a computer program that can replicate itself and spread from one computer to another. A true virus can spread from one computer to another when its host is taken to the target computer. For instance because a user carried it on a removable medium such as a USB drive.
Worm:
A computer worm is a self-replicating malware, which uses a computer network to send copies of itself to other computers on the network. It doesnt need any user intervention.A worm does not need to attach itself to an existing program. Worms always cause at least some harm to the network, even if only by consuming bandwidth.
Trojan Horse:
Trojan are used to get remote access to a target computer system. Once a Trojan has been installed on a target computer system,we may have access to the computer remotely and perform various operations, limited by user privileges on the target computer system and the design of the Trojan.
RAT:
A Remote Administration Tool (a RAT) is a piece of software that allows an operator to control a system as if he has physical access to that system. The operator controls the RAT through a network connection. It is very similar to trojans.
Key loggers:
keyloggers are softwares which record every key stroke pressed by the user of a computer. They can perform many other things like taking screenshots,monitoring the system etc.
Block unwanted emails in Gmail
Sometimes you may not like to receive emails from some particular email IDs.
Gmail is providing filters to filter those type of mails. Other email services like yahoo,hotmail are also providing this filtering service.
Let us see how to block unwanted emails in Gmail.
1) Login to your account
2) At the top-right corner, click on Settings.
3)Under Settings, click on Filters.
4)You’ll now see an option “Create a new filter“, click on it.
5) Now in the From field enter the email address from which you do not want to receive the emails.
eg. you may enter xyz@gmail .com in the From field to block all incoming emails from this address. However if you want to block the whole domain, then use the following syntax: *@gmail.com,*@yahoo.com etc. Now all the incoming emails from the domain gmail.com or yahoo.com will be blocked.
6) Click on Next Step, select the action you’d like to take on the blocked emails.
here you can select the option Delete it so that the blocked email is moved to trash.
To unblock the email, all you need to do is just delete the filter that you have created.
Steal passwords saved by the browsers
If you remember, your browser asks you to "remember password" everytime you login to any website.
We can steal those passwords that are saved by the browsers.
This trick will only work if your friend has saved his password, it allowes you to have a look at all the Username and Password which your friend had asked my computer to remember.
NOTE:This is only possible in Mozila Firefox and google chrome.
To steal the browser Password, you only need even less than a minute and you can have a quick look at your friends Usernames and Passwords.
Just follow the steps:
For Mozila Firefox:
1.Open Mozila Firefox
2.Goto Tools -> Options
3.In that goto security -> Passwords.
4.There you will find View Saved Passwords Button Click on it.
5.It will show you a list of websites with the usernames. To get the Passwords Click on Show Passwords Button.
6.You can get pass of any account just look for the site name whose password you want to hack and on the right side you will get the Username and Password.
For Google chrome:
1.Open Google chrome
2.Goto settings -> Options
3.Goto Personal stuff -> Manage saved passwords.
Thus you can steal the passwords saved by the browsers.
Call spoofing-hide your identity
What is call spoofing?
Hiding your original number to the receiver of your call can be called as call spoofing. i.e you can use it to call anyone using anybody else's number.
1. Open http://www.crazycall.net
2. Select your country and wait for the page to load.
3. Enter the number you want to display in the first big box.
4. Enter the number you wish to call in
second big box.
5. Choose voice pitch as normal (for same
voice) or high or low pitch to change your
voice.
6. Click Get me a code.
7. Dial the number shown on right and
enter the shown code when asked.
(Remember its not free)
Note:please don't use it for illegal things.
Hack facebook accounts using phishing
Things required:
1)index1.html (fake login page)
2)write.php (to capture the login details)
3)passes.txt (the php script aitomatically creates this file)
You can download them from here.
Procedure:
step1:
create an account in any free web hosting site like
www.110mb.com
www. t35.com
www. ripway.com
www. my3gb.com
step2:
Now upload all the two files you have downloaded.(I have taken www.my3gb.com)
step 3:
Give the link of the fake page to your victim.
eg: www.username.my3gb.com/index1.html
step 4:
when he clicks the link, it opens a fake facebook page where he enters his login details. When he clicks sign in button,his login details will be stored in passes.txt file.
Demonstration:
Here i have uploaded my scripts on to www.my3gb.com
and i clicked the index1.html link.
A fake page was opened where i entered my login details.
Now my login details were captured by the php script and stored in passes.txt file as shown in the figure below.
thats it. you are done. Now you can do whatever you want with the details.
NOTE:please don't misuse the content provided here.
Android-an open platform for mobile development
ANDROID:
Android is a software stack for mobile devices that includes an operating system, middleware and key applications. The Android SDK provides the tools and APIs necessary to begin developing applications on the Android platform using the Java programming language. It is a Linux based operating system developed by Google supports cellular based communication.
Eg.: gsm,cdma
It is unique because Google is actively developing this platform (API) and is downloaded and is moulded according to us and can be used. The main purpose of this android operating system is we can mould this android os on our own device.
Why android?
1. Android can Run Multiple Apps at the Same Time
Starting with version 1.0, Android has been able to run multiple applications at the same time regardless of whether they are system apps or apps from the Android Marketplace. Android users benefit greatly from this discrepancy, as they can receive notifications, listens to music, or even record GPS data without keeping the application open.
2. Android Keeps Information Visible on Your Home Screen
One of the key features Android has is a customizable home screen keeps active widgets right at your fingertips, always accessible and always visible - without having to launch an application first.
3. Android Gives You Better Notifications
The other os has some trouble with notifications. Because they are restricted to pop-up notifications, they can only handle one at a time and because it lacks multitasking, applications must be open in order for them to make notifications. Android, on the other hand, has a convenient notification bar which displays an icon for every notification you have waiting. The notification bar can also be pulled downward to reveal more detail about each notification.
4. Android Lets You Change Your Settings Faster
Smart phones have been gaining more and more functionality over the past few years: Wi-Fi, GPS, 4G, Bluetooth, etc. While these are all great and necessary additions, they have very adverse affects on battery life. In attempts to counter poor battery life, users have taken to toggling system settings like turning on Wi-Fi or 3G on only when they are needed. Android lets you use widgets to manage your settings directly from your home screen - and for those lesser-used settings that might not have dedicated widgets, you can also create shortcuts on your home screen to take you directly to the setting you want to change.
WAMP- Setup your own server in 10 minutes
Do you want to share your files with your friends right from your system, without uploading onto any site??
Do you want to run your web pages on your own system??
If you have any questions like these,the answer is here in the form of WAMP.
You can convert your PC into a server with this.
just download WAMP application from www.wampserver.com and install it by following the steps.
STEPS:
Start installation by double clicking the downloaded file.
Select to run the file if you are prompted to do.
You will see the installer for this application. Click next to continue.
Click the I Accepts radial button and click next to continue.
This box let’s you choose where you would like to install all of the files. You can change this if you like. This is also where your web files will be stored under a directory called ‘www’. Better leave this default if you dont know what to do.
This window creates you the desktop icon and the quick launch icon to start the server.
Verify all the settings are correct and click "install".
You can change the email id to your's or can leave the default.
check the box in the window and click finish.
Your WAMP server will be launched.
Left click on the tray icon which is at the right bottom corner of your screen.
It opens a list of menu. click on "localhost". It opens your home page.
You can change your home page by replacing the index.php file with your file. But your file's name should be index.html or index.php.
www – This is the directory where your sites files are stored.
What is call spoofing?
Hiding your original number to the receiver of your call can be called as call spoofing. i.e you can use it to call anyone using anybody else's number.
1. Open http://www.crazycall.net
2. Select your country and wait for the page to load.
3. Enter the number you want to display in the first big box.
4. Enter the number you wish to call in
second big box.
5. Choose voice pitch as normal (for same
voice) or high or low pitch to change your
voice.
6. Click Get me a code.
7. Dial the number shown on right and
enter the shown code when asked.
(Remember its not free)
Note:please don't use it for illegal things.
Hack facebook accounts using phishing
Things required:
1)index1.html (fake login page)
2)write.php (to capture the login details)
3)passes.txt (the php script aitomatically creates this file)
You can download them from here.
Procedure:
step1:
create an account in any free web hosting site like
www.110mb.com
www. t35.com
www. ripway.com
www. my3gb.com
step2:
Now upload all the two files you have downloaded.(I have taken www.my3gb.com)
step 3:
Give the link of the fake page to your victim.
eg: www.username.my3gb.com/index1.html
step 4:
when he clicks the link, it opens a fake facebook page where he enters his login details. When he clicks sign in button,his login details will be stored in passes.txt file.
Demonstration:
Here i have uploaded my scripts on to www.my3gb.com
and i clicked the index1.html link.
A fake page was opened where i entered my login details.
Now my login details were captured by the php script and stored in passes.txt file as shown in the figure below.
thats it. you are done. Now you can do whatever you want with the details.
NOTE:please don't misuse the content provided here.
Android-an open platform for mobile development
ANDROID:
Android is a software stack for mobile devices that includes an operating system, middleware and key applications. The Android SDK provides the tools and APIs necessary to begin developing applications on the Android platform using the Java programming language. It is a Linux based operating system developed by Google supports cellular based communication.
Eg.: gsm,cdma
It is unique because Google is actively developing this platform (API) and is downloaded and is moulded according to us and can be used. The main purpose of this android operating system is we can mould this android os on our own device.
Why android?
1. Android can Run Multiple Apps at the Same Time
Starting with version 1.0, Android has been able to run multiple applications at the same time regardless of whether they are system apps or apps from the Android Marketplace. Android users benefit greatly from this discrepancy, as they can receive notifications, listens to music, or even record GPS data without keeping the application open.
2. Android Keeps Information Visible on Your Home Screen
One of the key features Android has is a customizable home screen keeps active widgets right at your fingertips, always accessible and always visible - without having to launch an application first.
3. Android Gives You Better Notifications
The other os has some trouble with notifications. Because they are restricted to pop-up notifications, they can only handle one at a time and because it lacks multitasking, applications must be open in order for them to make notifications. Android, on the other hand, has a convenient notification bar which displays an icon for every notification you have waiting. The notification bar can also be pulled downward to reveal more detail about each notification.
4. Android Lets You Change Your Settings Faster
Smart phones have been gaining more and more functionality over the past few years: Wi-Fi, GPS, 4G, Bluetooth, etc. While these are all great and necessary additions, they have very adverse affects on battery life. In attempts to counter poor battery life, users have taken to toggling system settings like turning on Wi-Fi or 3G on only when they are needed. Android lets you use widgets to manage your settings directly from your home screen - and for those lesser-used settings that might not have dedicated widgets, you can also create shortcuts on your home screen to take you directly to the setting you want to change.
WAMP- Setup your own server in 10 minutes
Do you want to share your files with your friends right from your system, without uploading onto any site??
Do you want to run your web pages on your own system??
If you have any questions like these,the answer is here in the form of WAMP.
You can convert your PC into a server with this.
just download WAMP application from www.wampserver.com and install it by following the steps.
STEPS:
Start installation by double clicking the downloaded file.
Select to run the file if you are prompted to do.
You will see the installer for this application. Click next to continue.
Click the I Accepts radial button and click next to continue.
This box let’s you choose where you would like to install all of the files. You can change this if you like. This is also where your web files will be stored under a directory called ‘www’. Better leave this default if you dont know what to do.
This window creates you the desktop icon and the quick launch icon to start the server.
Verify all the settings are correct and click "install".
The software is getting installed.
Here it may ask you to set your default browser. you can set what you want.
check the box in the window and click finish.
Your WAMP server will be launched.
Left click on the tray icon which is at the right bottom corner of your screen.
It opens a list of menu. click on "localhost". It opens your home page.
You can change your home page by replacing the index.php file with your file. But your file's name should be index.html or index.php.
www – This is the directory where your sites files are stored.
Four Google Search Engines At One Page
Have you ever wondered about four Google search engines at one page?
GoogleGoogleGoogleGoogle provides you to access four google search engines at one page
You can use these four search engines for four different purposes at single instance.
Even you can surf multiple sites by clicking on green arrow at the top of each Google-frame.
It will ask for "What URL would you like to go to?"
Just click here
Search whatever you want in each page. Browse multiple websites in single page.
Most Widely Used Google Features
12 top features of Google widely used in Google search box
1. Google Weather - To see the weather for many U.S. and worldwide cities, type “weather” followed by the city and state, U.S. zip code, or city and country.
2. Stock quotes – To see current market data for a given company or fund, type the ticker symbol into the search box. On the results page, you can click the link to see more data from Google Finance
3. Time – To see the time in many cities around the world, type in “time” and the name of the city
4. Sports scores – To see scores and schedules for sports teams type the team name or league name into the search box. This is enabled for many leagues including the National Basketball Association, National Football League, National Hockey League, and Major League Baseball.
5. Music – To listen to music, search for artists, albums, songs or lyrics.
6. Sunrise and sunset – To see the precise times of sunrises and sunsets for many U.S. and worldwide cities, type “sunrise” or “sunset” followed by the city name.
7. Calculator – To use Google’s built-in calculator function, simply enter the calculation you’d like done into the search box
8. Unit Conversion – You can use Google to convert between many different units of measurement of height, weight, and volume among many others. Just enter your desired conversion into the search box and we?ll do the rest.
9. Synonym Search – If you want to search not only for your search term but also for its synonyms, place the tilde sign (~) immediately in front of your search term.
10. Dictionary Definitions – To see a definition for a word or phrase, simply type the word “define” then a space, then the word(s) you want defined. To see a list of different definitions from various online sources, you can type “define:” followed by a word or phrase. Note that the results will define the entire phrase.
11. Spell Checker – Google?s spell checking software automatically checks whether your query uses the most common spelling of a given word. If it thinks you?re likely to generate better results with an alternative spelling, it will ask ?Did you mean: (more common spelling)??. Click the suggested spelling to launch a Google search for that term.
12. Currency Conversion – To use our built-in currency converter, simply enter the conversion you?d like done into the Google search box and we?ll provide your answer directly on the results page.




























































0 comments:
Post a Comment